Hello everyone!
It been a while since the last time I wrote something here. This time I am writing you and trying to provide something else with value.
The latest posts here I was trying to inform you about threats and new critical CVEs. This time I want to present the new platform that I have created to solve my daily “Threat & CVE intelligence”. What does this mean?
I am trying to cover the morning information ingestion without being crazy about all the source in internet, it is why I have created my own tool and I want to share it with you.
If you still here and you want to know more about the platform… The idea is very simple, something where I can check the latest Critical CVEs, Threats, Statistics and Public Exploits really easy.
All that information as Security Analyst or even as a Pentester is very important because it will help us to keep updated about what is going on out there.
(If you are planning to create an account please remember your password because the reset password has not been implemented yet)
The platform - CVE Secure Hosting
Let’s start to take a look into the platform itself (To be able to access you will need to create a new account). The first thing we will see is the “Dashboard”:
The section is divided on different sections that provide different information:
Total Vulnerabilities Posted by NVD during the last 7 days.
New Vulnerabilities Posted Today.
Critical Vulnerabilities Posted Today.
Latest Threats: Here we will see the latest threats discovered being exploited in the wild with a lot of helpful information (Published Date, Importance, Affected Resources, Description and Solution).
Top 10 Critical Vulnerabilities: Here we will see the latest top 10 critical vulnerabilities posted.
In case that you would like to know the latest critical vulnerabilities you can just click on it and then you will be able to visualise them and of course, you will be able to click into the CVE to gather deeper information:
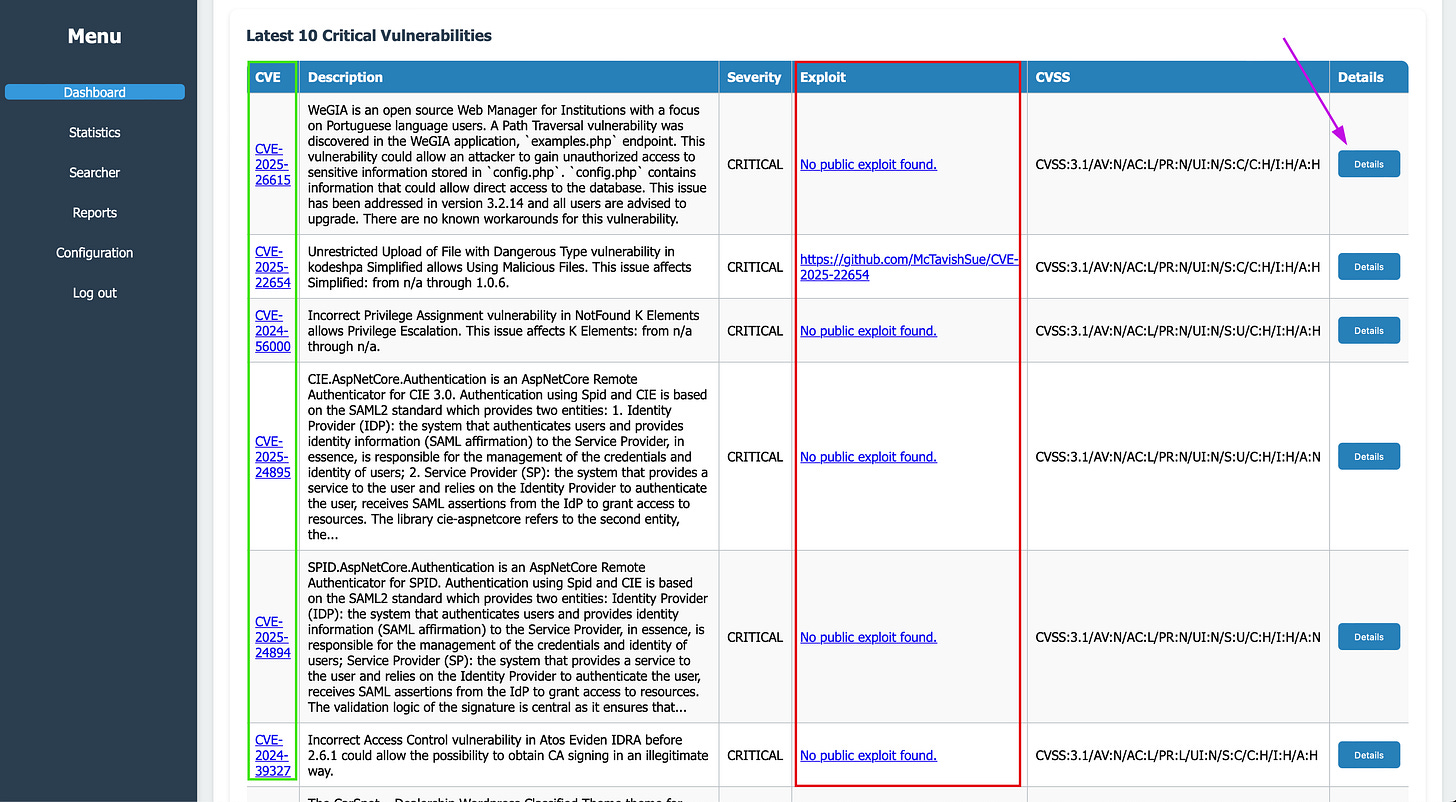
Then if we scroll down we will reach the “Top 10 Critical Vulnerabilities Section” where we will be able to see information like:
CVE ID.
Description.
Severity.
Possible Public Exploit.
CVSS.
Details: This part is very important because it will give you information about MITRE and CAPEC alignment.
For example, in case that we check the details of CVE-2025-26615, we will be able to match the CVE with MITRE ATT&CK and CAPEC. Also, we will be able to click on the link and reach the description with further information:
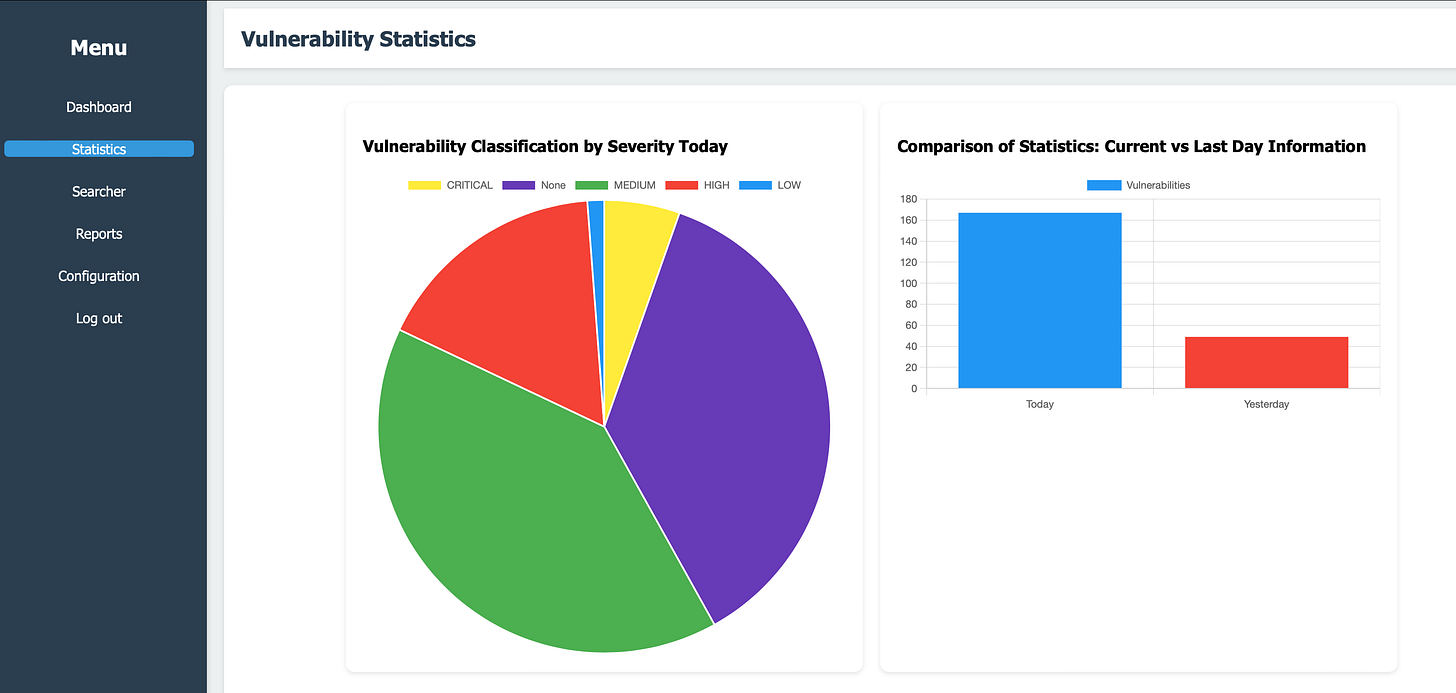
We have got a straightforward start. However, here is one of the most interesting parts, the statistics. Where we will find information like:
Vulnerability Classification By Severity Today: Classifies all the vulnerabilities posted the day that you have checked the tool by severity.
Comparison of Statistics: Current VS Last Day Information. Here we will compare the number of CVEs posted today with the CVEs posted yesterday.
Also, we have more information left:
Vulnerabilities by Category Today.
Vulnerabilities in Large Companies Today: As you can see in the screenshot, the CVEs are filtered to match large companies as well.
Lastly, in this section we have the latest critical vulnerabilities which have public exploits with information like:
CVE ID with the link.
Name the vulnerability (ID).
Description of the exploit.
Link to the exploit.
One of the last functions I have added to the platform is the searcher. What happens if you want to check other vulnerabilities? Then you can use the searcher, where you will have all the information that we have been checking before:
CVE ID.
Source Identifier.
Publication Date.
Status of the CVE.
Description.
Exploit: If there is a public exploit.
CVSS Version.
Vendor String.
Base Score.
Base Severity.
References
MITRE ATT&CK Techniques match.
MITRE CAPEC match.
Finally, you can generate a report (BETA version) where you will have all this information in a PDF:
Example:
I hope you liked the post and the tool! Feel free to reach me on any of my social network accounts. In case that you have any kind of issue with the tool or even any kind of advice, please reach me.
Happy Hacking & Defend Smart!