Welcome to our vibrant newsletter, your go-to source for the latest and most critical cybersecurity updates! This week, we've seen a dynamic cybersecurity landscape unfold, filled with vital information that every tech enthusiast and professional must know. From critical vulnerabilities that demand immediate action to fascinating comparisons with the past week's data, we've got you covered. Dive into our comprehensive analysis, where complex data is made understandable, ensuring you stay ahead in the cybersecurity game. Let's explore the pulse of the cyber world together! 🌐💻
All the information provided in this post has been extracted from the National Vulnerability Database (NVD) from National Institute of Standards and Technologies (NIST) from the government of US.
1. Weekly Vulnerabilities Overview
This week, we've identified a total of 647 vulnerabilities classified as follows:
Critical: 24 vulnerabilities
High: 90 vulnerabilities
Medium: 147 vulnerabilities
Low: 20 vulnerabilities
Others: 366 vulnerabilities
Conclusion: The prevalence of "Other" vulnerabilities highlights the diverse nature of threats, while the significant number of critical vulnerabilities underscores the urgent need for proactive security measures. It's crucial for individuals and organizations to stay vigilant and update their systems promptly. 🛡️
2. Comparative Vulnerability Analysis
Comparing the current week to the previous:
Critical vulnerabilities have seen a slight increase from 20 to 24.
High vulnerabilities rose from 68 to 90, marking a significant escalation.
Medium vulnerabilities decreased from 282 to 147.
Low vulnerabilities saw a reduction from 32 to 20.
Others dropped from 469 to 366.
Conclusion: The noticeable uptick in high and critical vulnerabilities demands increased attention from cybersecurity teams to mitigate potential threats effectively. The overall decrease in medium and low vulnerabilities is encouraging, but constant vigilance remains essential. 🚦
3. Vulnerabilities by Status
Awaiting Analysis: 631
Undergoing Analysis: 3
Analyzed: 4
Modified: 1
Rejected: 8
Conclusion: With the majority of vulnerabilities awaiting analysis, the cybersecurity community is reminded of the continuous need for research and understanding of emerging threats. The rejected vulnerabilities also highlight the critical role of discernment in identifying genuine threats. 🔍
4. Top 10 Companies by Reported Vulnerabilities
Mitre: 99 vulnerabilities
[Anonymous Company ID 416baaa9]: 85 vulnerabilities
Apple: 71 vulnerabilities
Google: 48 vulnerabilities
Wordfence: 47 vulnerabilities
VulDB: 35 vulnerabilities
GitHub: 34 vulnerabilities
Qualcomm: 22 vulnerabilities
Googlegroups: 16 vulnerabilities
Samsung: 14 vulnerabilities
Conclusion: The list of companies with the highest number of reported vulnerabilities underscores the ubiquitous nature of cybersecurity challenges across various industries. It's a call to action for all stakeholders to enhance their defensive mechanisms. 🏢
5. Vulnerabilities by Category
RCE (Remote Code Execution): 10 vulnerabilities
SQL Injection: 29 vulnerabilities
XSS (Cross-Site Scripting): 67 vulnerabilities
Insecure Deserialization: 0 vulnerabilities
Misconfiguration: 0 vulnerabilities
Conclusion: The dominance of XSS vulnerabilities indicates a widespread issue with web application security, emphasizing the need for robust input validation and sanitation practices. 🌐
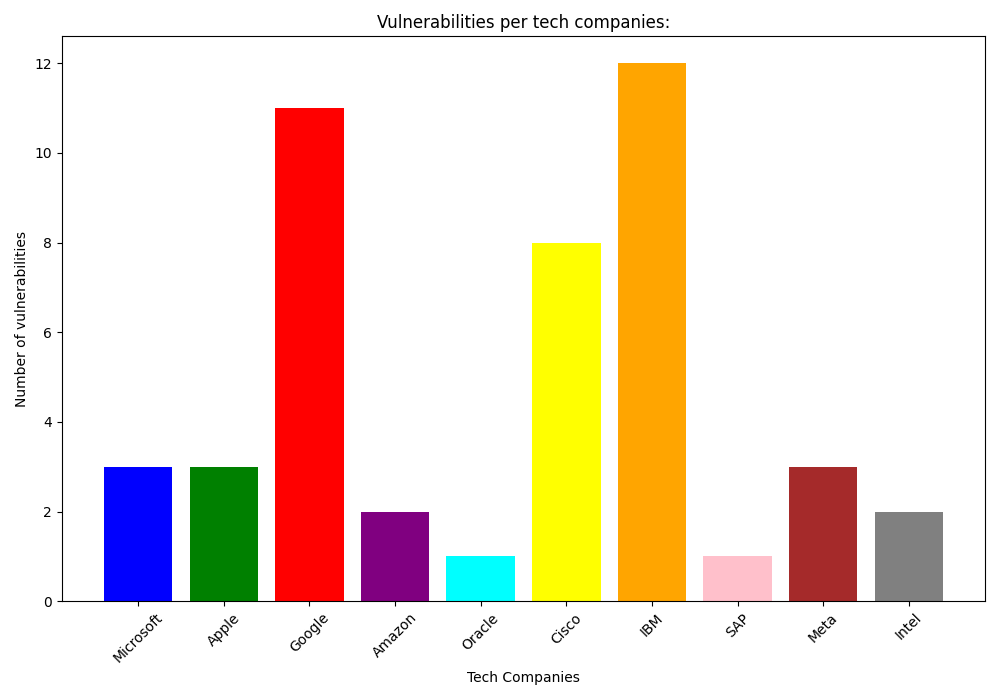
6. Vulnerabilities in Famous Companies
Microsoft: 3 vulnerabilities
Apple: 3 vulnerabilities
Google: 11 vulnerabilities
Amazon: 2 vulnerabilities
Cisco: 8 vulnerabilities
IBM: 12 vulnerabilities
Conclusion: Even the most prominent tech giants face significant cybersecurity challenges, highlighting the universal need for continuous improvement in security postures. 💼
7. Top 10 Critical Vulnerabilities
1. CVE-2023-28582: CRITICAL:9.8
Description: Memory corruption in Data Modem while verifying hello-verify message during the DTLS handshake.
Solution: Users should immediately contact their device manufacturer for firmware updates and apply any available patches to mitigate the vulnerability.
2. CVE-2023-43552: CRITICAL:9.8
Description: Memory corruption while processing MBSSID beacon containing several subelement IE.
Solution: Ensure your networking devices are updated to the latest firmware version provided by the manufacturer to address this issue.
3. CVE-2023-43553: CRITICAL:9.8
Description: Memory corruption while parsing beacon/probe response frame when AP sends more supported links in MLIE.
Solution: Keep wireless access points and network devices updated with patches from the device vendor to prevent exploitation.
4. CVE-2024-27198: CRITICAL:9.8
Description: Authentication bypass in JetBrains TeamCity before 2023.11.4 allowing admin actions.
Solution: Update to JetBrains TeamCity version 2023.11.4 or later, where this vulnerability has been addressed.
5. CVE-2023-7103: CRITICAL:9.8
Description: Authentication Bypass in ZKSoftware Biometric Security Solutions UFace 5.
Solution: Update to the latest version of the software provided by ZKSoftware, ensuring your system is beyond the vulnerable versions.
6. CVE-2024-27304: CRITICAL:9.8
Description: SQL injection in pgx, a PostgreSQL driver and toolkit for Go.
Solution: Upgrade to pgx version 4.18.2 or 5.5.4. Additionally, validate and sanitize input to prevent large queries from triggering this vulnerability.
7. CVE-2024-27307: CRITICAL:9.8
Description: JSONata before 1.8.7 and 2.0.4 allows property override via transform operator.
Solution: Update JSONata to version 1.8.7 or 2.0.4 immediately. Evaluate expressions securely and apply patches if you're unable to upgrade.
8. CVE-2024-28222: CRITICAL:9.8
Description: Inadequate validation of file path in Veritas NetBackup before 8.1.2 and Appliance before 3.1.2.
Solution: Update to Veritas NetBackup 8.1.2 or NetBackup Appliance 3.1.2 or later versions where this vulnerability is fixed.
9. CVE-2024-21899: CRITICAL:9.8
Description: Improper authentication in QNAP operating system versions.
Solution: Update to the specified QNAP firmware versions or later to mitigate this vulnerability:
QTS 5.1.3.2578 build 20231110 and later
QuTS hero h5.1.3.2578 build 20231110 and later
QuTScloud c5.1.5.2651 and later
10. CVE-2024-2184: CRITICAL:9.8
Description: Buffer overflow in Small Office Multifunction Printers and Laser Printers.
Solution: Contact the manufacturer for firmware updates addressing this vulnerability. Ensure that your printer firmware is updated to versions later than those listed as vulnerable.
Conclusion: These critical vulnerabilities pose a significant risk and require immediate attention to prevent potential exploits. Users and administrators are advised to follow the provided solutions and update their systems as soon as possible. 🔐
8. Public Exploits for Top 10 Vulnerabilities
CVE-2024-27198 involves an authentication bypass vulnerability in JetBrains TeamCity before 2023.11.4, allowing unauthorized admin actions. Here's a closer look at available public exploits:
CVE-2024-27198-RCE by W01fh4cker
Description: This repository contains an exploit for authentication bypass leading to Remote Code Execution (RCE) in JetBrains TeamCity versions prior to 2023.11.4.
This exploit demonstrates how an attacker can bypass authentication and execute arbitrary code on the server running the vulnerable TeamCity version.
CVE-2024-27198 by yoryio
Description: An exploit script for CVE-2024-27198 targeting TeamCity Server.
This repository offers a practical exploit script, showcasing the steps an attacker might take to exploit the vulnerability on affected TeamCity servers.
CVE-2024-27198 by Chocapikk
Description: Proof of Concept (PoC) for the authentication bypass in JetBrains TeamCity before 2023.11.4.
This PoC provides a detailed walkthrough of the authentication bypass, offering insights into how the vulnerability can be triggered.
CVE-2024-27198-EXPLOIT by K3ysTr0K3R
Description: A PoC exploit for CVE-2024-27198 showcasing JetBrains TeamCity authentication bypass.
Aimed at security researchers and professionals, this repository details the exploitation process, emphasizing the severity of the vulnerability.
CVE-2024-27198 by rampantspark
Description: A golang-based PoC for CVE-2024-27198.
This exploit showcases an alternative approach using Go, providing a different perspective on exploiting the vulnerability effectively.
These repositories contain valuable information and tools for understanding, researching, and potentially mitigating the risks associated with CVE-2024-27198. It's important for organizations and individuals affected by this vulnerability to review these resources and take appropriate action to secure their systems. Remember, responsible disclosure and usage of exploit information is crucial in the fight against cyber threats. Always use this information for defensive purposes and to enhance security postures.
Pattern Analysis and Conclusion
This week's cybersecurity landscape has been marked by an increased focus on high and critical vulnerabilities, emphasizing the ever-evolving nature of cyber threats. The comparative analysis reveals a dynamic shift in threat types, with a notable rise in high severity issues. Companies, regardless of their size or industry, are continuously targeted, demonstrating the universal risk of cyber threats. The detailed breakdown by category and status provides a clear call to action for enhanced vigilance and proactive security measures.
It's imperative for everyone to stay informed and take immediate action to update and secure their systems. Remember, cybersecurity is a shared responsibility, and staying ahead of threats requires collective awareness and action. Stay safe and secure in the digital world! 🌍🔒