🌟 Introduction
Welcome to this week's edition of the Cybersecurity Weekly Pulse, your go-to source for the latest and most critical updates in the world of cybersecurity! This week, we've seen a diverse array of vulnerabilities making headlines, from critical security flaws affecting major software and hardware vendors to intriguing patterns in vulnerability reporting and exploitation trends. Join us as we dive deep into the data, compare week-over-week changes, and provide you with actionable insights to keep your digital life secure. Let's get energized and informed! 🚀
All the information provided in this post has been extracted from the National Vulnerability Database (NVD) from National Institute of Standards and Technologies (NIST) from the government of US.
1️⃣ Weekly Vulnerability Insights
This week, we've identified a total of 659 vulnerabilities categorized as follows:
199 Others
22 Low
219 Medium
177 High
42 Critical
Conclusion: With a notable number of critical vulnerabilities, it's imperative for users and organizations to stay vigilant and prioritize updates and patches. The significant presence of medium and high-severity issues also underscores the constant need for robust security measures. 🛡️
2️⃣ Comparative Analysis of Vulnerabilities
Comparing the current week to the last:
Others: Increased from 143 to 199
Low: Slightly up from 20 to 22
Medium: Decreased from 263 to 219
High: Increased from 122 to 177
Critical: Decreased from 57 to 42
Conclusion: This week shows a mixed trend with increases in high-severity vulnerabilities but a decrease in critical ones. This pattern suggests a dynamic cybersecurity landscape where threat levels fluctuate. Staying informed is key! 🔍
3️⃣ Vulnerability Status Classification
Vulnerabilities by status paint a detailed picture of the cybersecurity workflow:
Received: 135
Awaiting Analysis: 441
Undergoing Analysis: 0
Analyzed: 36
Modified: 0
Deferred: 0
Rejected: 48
Conclusion: The bulk of vulnerabilities are awaiting analysis, highlighting the ongoing challenge for security teams to triage and address threats efficiently. The high rejection rate also suggests stringent criteria for vulnerability acceptance. 📊
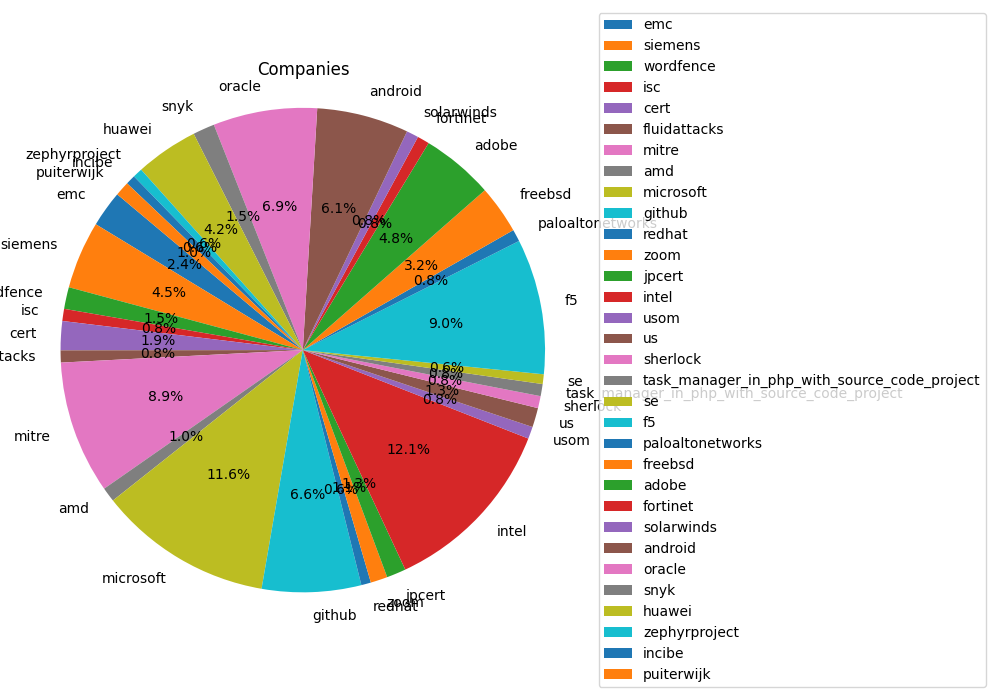
4️⃣ Top 10 Reporting Companies
The frontline defenders, reporting the most vulnerabilities:
Intel: 75 vulnerabilities
Microsoft: 72 vulnerabilities
F5: 56 vulnerabilities
Mitre: 55 vulnerabilities
Oracle: 43 vulnerabilities
GitHub: 41 vulnerabilities
Android: 38 vulnerabilities
Adobe: 30 vulnerabilities
Siemens: 28 vulnerabilities
Huawei: 26 vulnerabilities
Conclusion: Tech giants continue to lead in vulnerability reports, underscoring the complexity and wide usage of their products. It's crucial for users of these platforms to apply security updates promptly. 🔝
5️⃣ Vulnerabilities by Category
A closer look at the nature of vulnerabilities:
RCE (Remote Code Execution): 53 vulnerabilities
SQL Injection: 39 vulnerabilities
XSS (Cross-Site Scripting): 35 vulnerabilities
Insecure Deserialization: 0 vulnerabilities
Misconfiguration: 0 vulnerabilities
Conclusion: RCE, SQL Injection, and XSS dominate the landscape, signaling that traditional web vulnerabilities remain a significant threat. Awareness and preventive measures against these attacks are essential. 🌐
6️⃣ Famous Companies' Vulnerability Count
Notable companies on the radar
:
Microsoft: 43 vulnerabilities
Apple: 0 vulnerabilities
Google: 0 vulnerabilities
Amazon: 0 vulnerabilities
Oracle: 43 vulnerabilities
Cisco: 0 vulnerabilities
Adobe: 6 vulnerabilities
IBM: 8 vulnerabilities
SAP: 2 vulnerabilities
Meta: 0 vulnerabilities
Intel: 78 vulnerabilities
Conclusion: Microsoft, Oracle, and Intel show significant vulnerability counts, indicating the widespread impact of their products and the importance of safeguarding against potential exploits. 🌍
7️⃣ Top 10 Critical Vulnerabilities
The most severe vulnerabilities demanding immediate attention, along with solutions for end-users:
CVE-2024-1597: CRITICAL:10.0
Description: The PostgreSQL JDBC Driver, pgjdbc, has a critical SQL injection vulnerability when using PreferQueryMode=SIMPLE. This mode does not represent the default configuration, but if exploited, it allows an attacker to execute arbitrary SQL commands by bypassing parameterized query protections.
Impact: Potential for unauthorized data access, data manipulation, and in severe cases, complete database compromise.
Solution: Users are advised to update pgjdbc to versions 42.7.2, 42.6.1, 42.5.5, 42.4.4, 42.3.9, or 42.2.8 where this vulnerability is patched.
CVE-2024-23816: CRITICAL:9.8
Description: A hardcoded secret in the computation of a Keyed-Hash Message Authentication Code (HMAC) in various versions of Location Intelligence Perpetual and SUS products could allow an unauthenticated remote attacker to gain full administrative access.
Impact: Complete unauthorized access and control over the affected applications.
Solution: Upgrade to version V4.3 of the affected products to mitigate this vulnerability.
CVE-2024-21401: CRITICAL:9.8
Description: Microsoft Entra Jira Single-Sign-On Plugin Elevation of Privilege Vulnerability.
Impact: Attackers could exploit this vulnerability to elevate their privilege level, potentially gaining unauthorized access to sensitive information or control over the system.
Solution: Apply the latest patches and updates provided by Microsoft for the Entra Jira Single-Sign-On Plugin.
CVE-2024-21410: CRITICAL:9.8
Description: Microsoft Exchange Server Elevation of Privilege Vulnerability.
Impact: This vulnerability allows attackers to perform actions with elevated privileges on the Exchange Server, potentially leading to data theft, system compromise, or further network infiltration.
Solution: Microsoft has released patches for Exchange Server; users should install these updates immediately.
CVE-2024-21413: CRITICAL:9.8
Description: Microsoft Outlook Remote Code Execution Vulnerability.
Impact: Exploitation could allow an attacker to execute arbitrary code in the context of the current user. If the user has administrative rights, an attacker could take control of the affected system.
Solution: Microsoft has provided updates to address this vulnerability in Outlook. Users are encouraged to apply these updates promptly.
CVE-2023-6441: CRITICAL:9.8
Description: SQL Injection vulnerability in UNI-PA University Marketing & Computer Internet Trade Inc. University Information System.
Impact: Allows for SQL injection, enabling attackers to manipulate database queries, access, modify, or delete database data unauthorizedly.
Solution: Update the University Information System to the latest version before 12.12.2023, where this issue is resolved.
CVE-2024-25214: CRITICAL:9.8
Description: Authentication bypass via crafted payload in Employee Management System v1.0.
Impact: Attackers can bypass authentication mechanisms, potentially gaining unauthorized access to the system.
Solution: No specific solution provided. Users should contact the vendor for updates or apply general security best practices like input validation and secure authentication mechanisms.
CVE-2024-25215: CRITICAL:9.8
Description: SQL injection vulnerability in Employee Management System v1.0 through the pwd parameter.
Impact: Allows attackers to execute arbitrary SQL commands, leading to unauthorized database access or manipulation.
Solution: Ensure input validation and parameterized queries are implemented. Contact the vendor for specific patches or updates.
CVE-2024-25216: CRITICAL:9.8
Description: SQL injection vulnerability in Employee Management System v1.0 via the mailud parameter.
Impact: Similar to CVE-2024-25215, this vulnerability could lead to unauthorized database operations.
Solution: Implement security best practices such as input validation and parameterized queries. Seek vendor guidance for patches.
CVE-2024-25220: CRITICAL:9.8
Description: SQL injection vulnerability in Task Manager App v1.0 via the taskID parameter.
Impact: Enables attackers to inject malicious SQL queries, compromising the database integrity.
Solution: No direct solution is provided. Users are recommended to apply secure coding practices and look for updates from the developer.
Final Thoughts: These vulnerabilities underscore the critical importance of maintaining up-to-date systems and applying security best practices. The diverse nature of these vulnerabilities, affecting software from database drivers to management systems, highlights the ever-present need for vigilance in cybersecurity practices. Users and administrators are urged to review these vulnerabilities closely and take the necessary preventative measures to protect their systems and data. Stay secure! 🔐🌐
8️⃣ Public Exploits for Top Vulnerabilities
The cybersecurity landscape is not only shaped by the discovery of vulnerabilities but also significantly influenced by the availability of public exploits. Such exploits provide both researchers and potential attackers with the means to leverage vulnerabilities, making the swift application of patches and mitigations even more critical. This week, we focus on CVE-2024-21413, for which multiple public exploits have been identified, indicating a heightened risk of active exploitation. Below, we detail these exploits and offer direct links to their repositories for further examination by security professionals.
CVE-2024-21413: Microsoft Outlook Remote Code Execution Vulnerability
Several repositories have been made available on GitHub, providing proof-of-concept (POC) codes or exploit details for CVE-2024-21413. This vulnerability, classified as CRITICAL with a severity score of 9.8, has seen significant interest from the cybersecurity community, underlining the urgency for users to apply available patches to mitigate potential risks.
Repository: CVE-2024-21413
Description: A repository dedicated to exploiting the Microsoft Outlook Information Disclosure Vulnerability, specifically targeting the leakage of password hashes through an Expect Script proof of concept.
Repository: CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability
URL: https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability
Description: Focuses on the remote code execution aspect of the vulnerability, providing a detailed exploit method.
Repository: CVE-2024-21413
Description: Another take on the Microsoft Outlook Information Disclosure Vulnerability, offering a POC for educational purposes within a TryHackMe Lab environment.
Repository: CVE-2024-21413
Description: Similar to other repositories, this one provides insights into exploiting the information disclosure vulnerability in Microsoft Outlook.
Repository: CVE-2024-21413-POC
Description: Offers a Proof of Concept script for exploiting the vulnerability to leak password hashes, emphasizing the practical application of the exploit.
Repository: CVE-2024-21413
Description: Provides a guide and tool for leveraging the CVE-2024-21413 vulnerability to capture login credentials, targeting Turkish-speaking users.
Repository: CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability
Description: While this repository's description is not provided, its title suggests a focus on remote code execution capabilities within Microsoft Outlook.
Conclusion: The presence of these publicly available exploits for CVE-2024-21413 highlights the critical need for awareness and rapid response among users and IT professionals. By applying the latest patches and adopting comprehensive security measures, potential damages from such vulnerabilities can be significantly mitigated. It is a stark reminder of the ever-evolving nature of cybersecurity threats and the importance of staying informed and prepared. Stay safe and secure in the digital space! 🔒🌍
🔍 Pattern Analysis and Final Thoughts
This week's cybersecurity landscape showcases a vibrant mix of threats and challenges. The fluctuation in vulnerability severity levels emphasizes the importance of adaptive security postures and continuous monitoring. With tech giants frequently appearing in reports, it's clear that their widespread use makes them prime targets for exploitation. The prevalence of traditional web vulnerabilities like RCE, SQL Injection, and XSS underlines the enduring need for fundamental security practices. As always, staying informed and proactive is your best defense in the digital realm. Stay safe, and see you next week for more updates! 🌐💼
Remember, cybersecurity is a journey, not a destination. Together, we can build a safer digital world. 🌍💡