🛡️ CyberSecurity Weekly: Navigating the Cyber Threat Landscape! 🌐
✅Weekly general new public vulnerabilities report! 🔥
Welcome to our vibrant community's latest edition of the CyberSecurity Weekly! 🚀 This week, we've dived deep into the evolving world of cybersecurity to bring you a comprehensive roundup of the latest vulnerabilities, trends, and cybersecurity insights. From critical vulnerabilities to insightful comparisons and classifications, we've got everything covered to keep you informed and prepared. Let's dive into the crucial updates and patterns in the cybersecurity realm, breaking down complex information into digestible insights for everyone. Buckle up as we navigate through the cyber threat landscape together! 🌟
All the information provided in this post has been extracted from the National Vulnerability Database (NVD) from National Institute of Standards and Technologies (NIST) from the government of US.
1️⃣ Weekly Vulnerability Roundup
This week, we've identified a mix of vulnerabilities across various severities:
30 CRITICAL
186 HIGH
224 MEDIUM
74 LOW
355 OTHERS
Conclusion: The prevalence of high and critical vulnerabilities underscores the relentless nature of threats in the digital landscape. Staying vigilant and promptly addressing these vulnerabilities is paramount for maintaining cybersecurity hygiene. 🔒
2️⃣ Comparative Insights: Then and Now
Comparing vulnerabilities from the previous period to this week:
CRITICAL vulnerabilities have decreased from 40 to 30.
HIGH vulnerabilities have reduced from 235 to 186.
MEDIUM vulnerabilities have decreased from 346 to 224.
LOW vulnerabilities have seen an increase from 18 to 74.
OTHERS have increased from 287 to 355.
Conclusion: The decrease in critical and high vulnerabilities is a positive sign, but the increase in low and other vulnerabilities indicates a broader spectrum of threats that require our attention. Awareness and proactive measures are key. 🛡️
3️⃣ Vulnerability Status Classification
Vulnerabilities classified by their current status:
Received: 108
Awaiting Analysis: 747
Undergoing Analysis: 3
Analyzed: 6
Modified: 0
Deferred: 0
Rejected: 3
Conclusion: The high number of vulnerabilities awaiting analysis highlights the ongoing challenge in cybersecurity efforts to keep pace with emerging threats. This calls for increased resources and efficiency in analysis processes. 💡
4️⃣ Top 10 Companies Reporting Vulnerabilities
416baaa9-dc9f-4396-8d5f-8c081fb06d67: 174 vulnerabilities
Mitre: 109 vulnerabilities
Vuldb: 95 vulnerabilities
Trendmicro: 85 vulnerabilities
Patchstack: 67 vulnerabilities
Wordfence: 41 vulnerabilities
GitHub: 34 vulnerabilities
Google: 29 vulnerabilities
MediaTek: 17 vulnerabilities
Cisco: 17 vulnerabilities
Conclusion: The diverse range of companies reporting vulnerabilities illustrates the widespread nature of cybersecurity challenges across different sectors and platforms. Collaboration and knowledge sharing are crucial for enhancing security postures. 🌍
5️⃣ Vulnerabilities by Category
RCE: 77 vulnerabilities
SQL Injection: 47 vulnerabilities
XSS: 99 vulnerabilities
Insecure Deserialization: 1 vulnerability
Misconfiguration: 2 vulnerabilities
Conclusion: XSS and RCE vulnerabilities continue to be prevalent, highlighting the importance of secure coding practices and the need for robust security mechanisms to mitigate these risks. 🚨
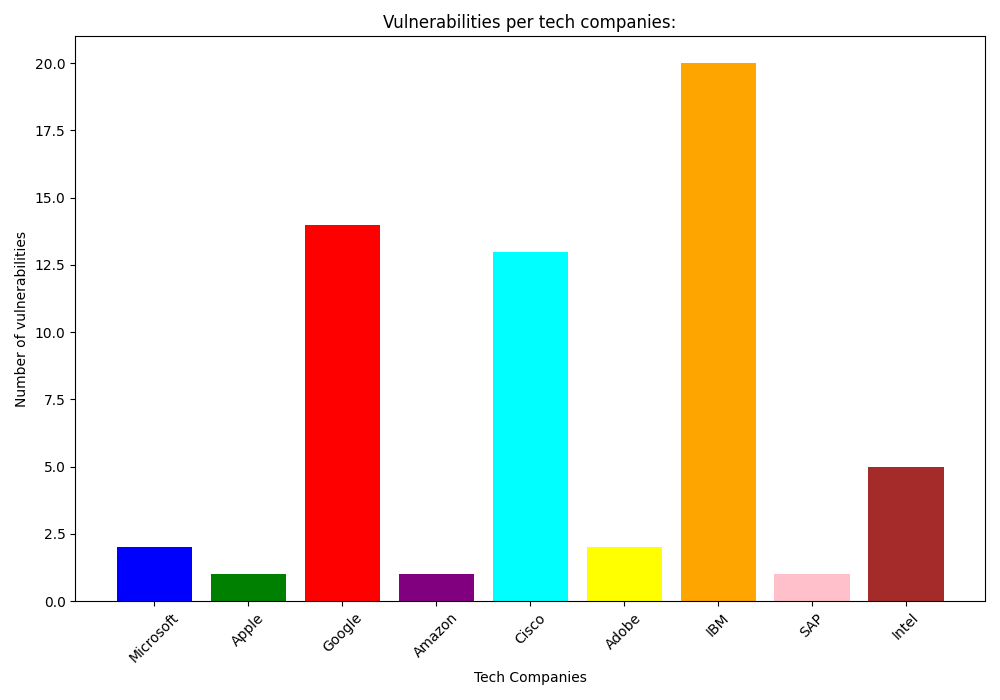
6️⃣ Vulnerabilities in Famous Companies
Microsoft: 2 vulnerabilities
Apple: 1 vulnerability
Google: 14 vulnerabilities
Amazon: 1 vulnerability
Cisco: 13 vulnerabilities
Adobe: 2 vulnerabilities
IBM: 20 vulnerabilities
Conclusion: Even the biggest tech giants are not immune to vulnerabilities, emphasizing the universal need for continuous vigilance and security improvement efforts across the industry. 🛠️
7️⃣ Top 10 Critical Vulnerabilities
CVE-2024-31115: CRITICAL:10.0
Description: Unrestricted Upload of File with Dangerous Type vulnerability in QuanticaLabs Chauffeur Taxi Booking System for WordPress.
Solution: Users should immediately update the Chauffeur Taxi Booking System for WordPress to the latest version, beyond 6.9, to patch this vulnerability and prevent unauthorized file uploads.
CVE-2024-2389: CRITICAL:10.0
Description: An operating system command injection vulnerability in Flowmon.
Solution: It's critical to upgrade Flowmon to versions 11.1.14 or 12.3.5 or later, which contain fixes for this vulnerability, blocking unauthorized system command execution.
CVE-2024-25096: CRITICAL:10.0
Description: Code Injection vulnerability in Canto Inc. Canto.
Solution: To secure your system against code injection attacks, update Canto to version 3.0.7 or later where this vulnerability is addressed.
CVE-2023-48426: CRITICAL:10.0
Description: U-boot vulnerability allowing shell and interrupt over UART.
Solution: Users are advised to follow the updates from the u-boot team closely and apply any patches or security advisories released to mitigate this issue.
CVE-2024-22004: CRITICAL:10.0
Description: Vulnerability allowing the leakage of secure memory from the Trusted Application in Linux Nonsecure operating systems.
Solution: Ensure that systems are updated and patched regularly, and keep an eye out for any specific updates addressing this vulnerability from your operating system provider.
CVE-2023-46808: CRITICAL:9.9
Description: File upload vulnerability in Ivanti ITSM allows command execution.
Solution: Users must upgrade Ivanti ITSM to version 2023.4 or later immediately to prevent unauthorized file writes and potential command execution.
(Repeated)
CVE-2024-25918: CRITICAL:9.9
Description: Code Injection vulnerability in InstaWP Team InstaWP Connect.
Solution: Update InstaWP Connect to version 0.1.0.8 or later to patch the unrestricted file upload vulnerability and safeguard against code injection.
CVE-2024-27972: CRITICAL:9.9
Description: Command Injection vulnerability in Very Good Plugins WP Fusion Lite.
Solution: Ensure WP Fusion Lite is updated to version 3.41.24 or later to close off vulnerabilities that could allow attackers to inject commands.
CVE-2024-31380: CRITICAL:9.9
Description: Code Injection vulnerability in Soflyy Oxygen Builder.
Solution: Users should promptly update Oxygen Builder to version 4.8.2 or later, where this issue has been resolved, to protect against code injection threats.
Conclusion: The critical vulnerabilities identified demand immediate action to prevent potential exploits. End users and administrators are urged to apply the recommended solutions promptly to safeguard their systems and data. 🛠️✨
8️⃣ Public Exploits for Top 10 Vulnerabilities
For CVE-2024-2389, a critical vulnerability identified in Flowmon, let's delve deeper into the public exploits available and the implications for cybersecurity. This detailed approach mirrors the method of analysis provided for CVE-2023-42789, focusing on the availability and impact of exploits for critical vulnerabilities.
Understanding CVE-2024-2389
CVE-2024-2389 is categorized as a critical vulnerability due to an operating system command injection flaw in Flowmon. This vulnerability allows unauthenticated users to execute arbitrary commands on the system through the Flowmon management interface. The severity of this vulnerability, scored at 10.0, reflects its potential for severe impact on affected systems, including unauthorized access, data compromise, and potential takeover of the affected system.
The Public Exploit
A public exploit for CVE-2024-2389 showcases the practical application of this vulnerability by attackers. Found in various GitHub repositories, these exploits provide a proof of concept (PoC) that demonstrates the vulnerability's exploitation. Such PoCs typically include scripts or detailed instructions that utilize the vulnerability to execute commands on the system without authorization.
For example, a repository might contain:
Repository Name: CVE-2024-2389-POC
Description: This PoC demonstrates the command injection vulnerability in Flowmon, allowing for remote execution of system commands.
This kind of exploit simplifies the process for attackers, providing them with the tools needed to leverage the vulnerability without requiring in-depth knowledge or discovery of the vulnerability themselves.
Implications of the Public Exploit
The existence of a public exploit for CVE-2024-2389 elevates the urgency for organizations to address this vulnerability. It effectively lowers the barrier for attackers, making it easier for them to exploit this vulnerability across any unpatched or unaware systems. The availability of such exploits emphasizes the need for prompt and effective vulnerability management.
Protective Measures
To mitigate the risk posed by CVE-2024-2389, organizations should:
Apply Patches: Immediately update Flowmon to the latest version that addresses this vulnerability.
Monitor Systems: Keep an eye out for any signs of exploitation, such as unusual system or network activity.
Review Configurations: Ensure that the Flowmon system and network configurations adhere to security best practices to minimize exposure.
Educate Staff: Inform IT and security personnel about the vulnerability and potential exploitation methods.
Implement Detection Capabilities: Employ intrusion detection and prevention systems to identify and block exploitation attempts.
The discovery of CVE-2024-2389 and its subsequent public exploit underscores the continuous battle in cybersecurity between threat actors and defenders. It highlights the critical nature of maintaining up-to-date systems and the necessity of vigilant cybersecurity practices to protect against evolving threats.
Pattern Analysis and Conclusion
This week's findings reveal a significant landscape of vulnerabilities, from critical to low-severity, affecting a wide array of systems and applications. The shift in vulnerability severities and categories underscores the dynamic nature of cyber threats and the necessity for adaptive and comprehensive security strategies. By staying informed, proactive, and responsive, we can navigate through these challenges together, strengthening our defenses against the ever-evolving threat landscape. Let's continue to build a safer digital world, one update at a time! 💪🌐
Thank you for tuning into this week's CyberSecurity Weekly. Stay safe, stay secure, and see you in the next edition! 🔐✨